Addressing Vulnerabilities: The Importance of Proactive Measures in Preventing Security Breaches like Orbiter Finance
In today’s digital landscape, the threat of security breaches and cyber attacks looms large. With hackers becoming increasingly sophisticated, it is imperative for businesses to implement proactive security measures to address vulnerabilities before they can be exploited.
Why is proactive security so essential?
By taking a proactive approach to security, businesses can stay one step ahead of potential attackers. This involves identifying vulnerabilities in their systems and networks, and implementing measures to patch these weaknesses. It’s not enough to simply react to security incidents after they occur; businesses must be proactive in preventing them from happening in the first place.
The consequences of a security breach can be devastating, both financially and reputationally. Data breaches can result in the loss of valuable customer information, financial losses, and legal consequences. Additionally, businesses may suffer long-term damage to their reputation, leading to a loss of customer trust.
How can businesses implement proactive security measures?
There are several crucial steps businesses can take to enhance their security posture:
- Regular vulnerability assessments: Conducting regular assessments can help identify weaknesses and vulnerabilities in systems and networks.
- Implementing strong access controls: Limiting access to sensitive information and ensuring employees follow strong password policies can significantly reduce the risk of unauthorized access.
- Continuous monitoring: Utilizing robust monitoring tools and systems can help detect and respond to threats in real-time.
- Employee training: Educating employees about best practices for security can help minimize the risk of human error leading to a security breach.
- Regular software updates: Keeping software and systems up to date with the latest patches and security updates is vital to prevent exploitable vulnerabilities.
By implementing these proactive security measures, businesses can significantly reduce the risk of security breaches and protect their valuable assets.
Ultimately, the importance of proactive security measures cannot be overstated. In an evolving threat landscape, businesses must stay vigilant and continuously adapt their security strategies to address vulnerabilities effectively.
Understanding Security Vulnerabilities
When it comes to ensuring the security of your systems and data, it is crucial to have a comprehensive understanding of the potential vulnerabilities that may expose them to security breaches.
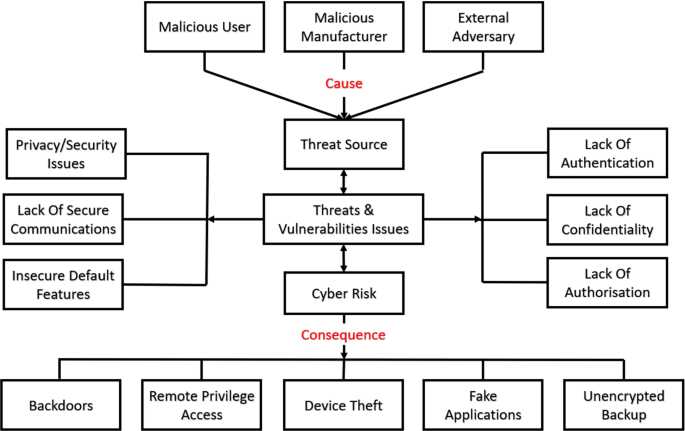
A security vulnerability refers to a weakness or flaw in a system or application that can be exploited by cybercriminals to gain unauthorized access, manipulate data, or disrupt operations. These vulnerabilities can be present in various components of a system, such as software, hardware, networks, and even human interactions.
There are different types of security vulnerabilities that organizations need to be aware of:
1. Software Vulnerabilities: These vulnerabilities exist in the code of applications or operating systems and arise due to programming errors or design flaws. They can include buffer overflows, SQL injections, cross-site scripting (XSS), and other similar weaknesses.
2. Hardware Vulnerabilities: These vulnerabilities refer to weaknesses in the physical components of a system, such as computer processors, memory modules, or input/output devices. Hardware vulnerabilities can be exploited by attackers to bypass security measures and gain unauthorized access.
3. Network Vulnerabilities: These vulnerabilities are related to the security of networks and their infrastructure. They can include weak passwords, misconfigured routers or firewalls, unencrypted data transmission, or insecure wireless networks. Exploiting network vulnerabilities can allow attackers to intercept or modify data traffic, launch denial-of-service attacks, or gain unauthorized access to network resources.
4. Human Vulnerabilities: Humans can be a weak link in the security chain, as they can unknowingly introduce vulnerabilities through their actions or negligence. This can include falling for phishing scams, using weak passwords, sharing sensitive information, or improperly handling data.
Understanding these vulnerabilities is the first step towards implementing effective security measures. By identifying and addressing weaknesses in software, hardware, networks, and human behavior, organizations can significantly reduce the risk of security breaches.
Remember, proactive security measures are essential to protect your systems and data from potential threats. Stay vigilant, keep your systems up to date, and regularly educate your employees on best security practices to minimize vulnerabilities and maintain a secure environment.
The Importance of Identifying Weak Points

Identifying weak points in your security system is crucial in ensuring the overall protection of your business or organization.
Just like any structure, a security system is only as strong as its weakest point. Without identifying these weak points, you leave your business vulnerable to potential security breaches.
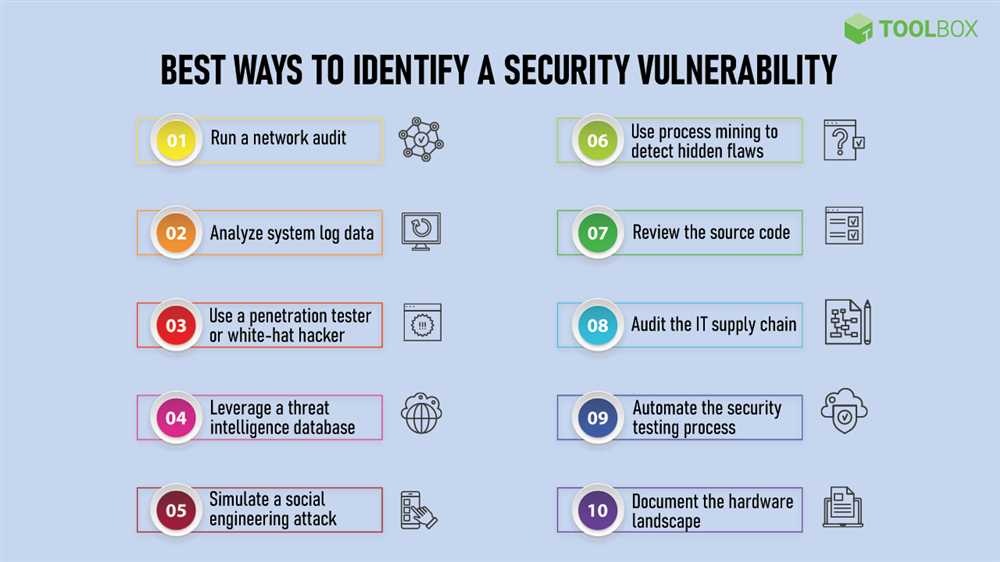
By conducting regular vulnerability assessments, you can pinpoint the areas where your security measures may be lacking.
Weak points can exist in various aspects of your security system, such as outdated software, unencrypted data, or insufficient employee training. These vulnerabilities can be exploited by hackers or malicious actors, putting sensitive information and assets at risk.
Identifying weak points also allows you to prioritize and allocate resources to strengthen your security measures in the right areas.
Implementing regular risk assessments, penetration testing, and security audits are effective ways to identify weak points and uncover potential vulnerabilities.
Once weak points have been identified, it is essential to take proactive measures to address them. This may involve updating software, implementing stronger access controls, or educating employees on the importance of cybersecurity.
Remember, being proactive in identifying and addressing weak points in your security system can help prevent security breaches and safeguard your business from potential threats.
The Risks of Ignoring Vulnerabilities
Vulnerabilities within a system can pose serious risks to the overall security and integrity of an organization. Ignoring these vulnerabilities can have severe consequences, both financially and reputationaly. By failing to address vulnerabilities and take proactive security measures, businesses expose themselves to potential security breaches that could lead to the loss of sensitive data, intellectual property theft, and even legal ramifications.
Financial Loss
Ignoring vulnerabilities can result in significant financial loss for an organization. Exploiting security vulnerabilities can lead to unauthorized access to customer data, leading to potential legal action and costly penalties. Additionally, a security breach can disrupt business operations, causing downtime and loss of productivity, which can be expensive to recover from.
Hiring a security team to identify and address vulnerabilities may seem like an unnecessary expense, but the potential cost of a security breach can prove far more damaging. Investing in proactive security measures can help minimize the financial risks associated with ignoring vulnerabilities.
Reputation Damage
A security breach can seriously damage an organization’s reputation. Customers and clients place a high value on the security of their data, and a breach can erode trust and confidence in a company. The negative publicity and public outcry that can follow a security breach can have long-lasting implications for a business, leading to a loss of customers, partners, and investors.
By proactively addressing vulnerabilities and implementing robust security measures, organizations can demonstrate their commitment to protecting sensitive information and maintaining the trust of their stakeholders. Investing in security now can help safeguard a company’s reputation for years to come.
Don’t underestimate the risks of neglecting vulnerabilities. Putting off security measures and ignoring vulnerabilities can have grave consequences. It’s essential for organizations to take a proactive approach to security and address vulnerabilities promptly to prevent potential security breaches. By doing so, businesses can protect their financial stability, reputation, and ultimately their future.
The Consequences of Security Breaches
In today’s technology-driven world, security breaches can have serious consequences for businesses, governments, and individuals alike. From financial losses and damaged reputations to compromised personal data and disrupted operations, the fallout from a security breach can be devastating.
One of the most immediate consequences of a security breach is the financial impact. Businesses can lose significant amounts of money as a result of theft, fraud, and the cost of investigating and mitigating the breach. This can include not only the direct financial losses but also the indirect costs associated with repairing any damage caused, implementing enhanced security measures, and regaining the trust of customers and clients.
Another consequence of security breaches is the damage to a company’s reputation. When a breach occurs, customers and clients may lose confidence in the organization’s ability to protect their sensitive information. This can lead to a loss of business and long-term damage to the company’s brand. It can take years to rebuild a tarnished reputation and win back the trust of customers.
Security breaches can also result in the theft or exposure of personal data. This can have serious consequences for individuals, who may become victims of identity theft or other types of fraud. Personal information such as social security numbers, bank account details, and passwords may be compromised, leaving individuals vulnerable to financial losses and other forms of exploitation. The emotional and psychological toll of such breaches should not be underestimated.
In addition to these immediate consequences, security breaches can also disrupt business operations. Systems may be shut down or compromised, leading to downtime and reduced productivity. In some cases, businesses may be unable to access their critical data or perform necessary functions, resulting in significant disruption and financial losses.
It is clear that the consequences of security breaches are far-reaching and can have long-lasting effects. It is essential for organizations and individuals to prioritize proactive security measures to prevent breaches and minimize the potential damage. This includes implementing robust security protocols, training employees on best practices, and staying informed about emerging threats.
By understanding the potential consequences of security breaches, businesses and individuals can better appreciate the importance of investing in strong security measures. The cost of prevention is far less than the cost of response and recovery in the aftermath of a breach.
Proactive Security Measures
When it comes to security, it is essential to be proactive rather than reactive. By taking the necessary precautions, you can prevent security breaches and protect your sensitive data. Here are some key proactive security measures to implement:
1. Regular Security Audits
Performing regular security audits is crucial to identify vulnerabilities and weaknesses in your system. This helps you stay one step ahead of potential threats and allows you to address any issues before they can be exploited.
2. Employee Education and Training
One of the most significant security risks is human error. By providing comprehensive education and training to your employees on security practices, you can significantly reduce the likelihood of accidental breaches. Teach them about password hygiene, phishing attacks, and the importance of keeping software up to date.
3. Secure Network Infrastructure
Ensuring that your network infrastructure is adequately secured is a critical proactive security measure. Implementing strong firewalls, intrusion detection systems, and regular network monitoring can help detect and prevent unauthorized access and potential security breaches.
4. Data Encryption
Encrypting sensitive data is an effective way to protect it from unauthorized access. Implementing encryption safeguards ensures that even if a breach occurs, the data remains unreadable and unusable to the attacker.
5. Regular Software Updates
Keeping software and applications up to date is vital for maintaining security. Software updates often include patches and bug fixes that address vulnerabilities discovered over time. Failure to update may leave your system exposed to known threats.
Implementing these proactive security measures can significantly reduce the risk of security breaches and protect your valuable data. By addressing vulnerabilities before they can be exploited, you can ensure the continued security and stability of your system.
Preventing Vulnerabilities before they Occur
In today’s rapidly evolving technological landscape, it is essential for businesses to stay ahead of potential risks and vulnerabilities. By implementing proactive security measures, organizations can significantly reduce the chances of security breaches and protect sensitive information from falling into the wrong hands.
One of the key steps in preventing vulnerabilities is conducting regular risk assessments. By identifying potential weaknesses and vulnerabilities within their systems, businesses can take necessary actions to mitigate these risks before they become exploitable threats. This includes conducting penetration testing, vulnerability scanning, and implementing patches and updates to close any security gaps.
Another crucial aspect of preventing vulnerabilities is employee education and training. Many security breaches occur due to human error, such as clicking on malicious links or falling victim to social engineering attacks. By training employees on safe browsing habits, password security, and recognizing phishing attempts, businesses can significantly reduce the risk of human-caused vulnerabilities.
Furthermore, it is essential for businesses to stay up-to-date with the latest security practices and technologies. This includes regularly updating software and operating systems, implementing multi-factor authentication, encrypting sensitive data, and monitoring network traffic for any suspicious activities.
In conclusion, preventing vulnerabilities before they occur is crucial for businesses to maintain a secure and trustworthy environment. By conducting regular risk assessments, educating employees, and staying current with security practices, organizations can proactively address potential weaknesses and reduce the risk of security breaches.
The Role of Employee Training

When it comes to preventive security measures, one cannot underestimate the importance of employee training. While implementing robust security systems and measures is crucial, it is equally necessary to educate and train your employees on the best practices to prevent security breaches.
1. Awareness and Knowledge
Through employee training programs, your staff can gain the necessary awareness and knowledge regarding potential security vulnerabilities and threats. They will learn how to identify suspicious activities, phishing attempts, and social engineering tactics that cybercriminals may employ to gain unauthorized access to sensitive information. By being aware of these risks, your employees can remain vigilant and take immediate action to mitigate them.
2. Best Practices and Security Protocols

Employee training also helps establish standard security protocols and best practices within your organization. By educating your employees on the importance of creating strong, unique passwords, regularly updating software and applications, and adhering to secure browsing habits, you can significantly reduce the likelihood of security breaches. Training can also cover topics such as data backup procedures, secure remote access policies, and incident response plans, allowing your employees to respond effectively in case of a security incident.
It is worth noting that the effectiveness of employee training depends on the quality and regularity of the programs. Providing ongoing training sessions and keeping your staff up to date with the latest security trends and best practices are essential to maintain a proactive security culture within your organization.
In conclusion, employee training plays a crucial role in proactive security measures. By enhancing employees’ awareness, knowledge, and adherence to security protocols, your organization can minimize the risk of security breaches and ensure the protection of sensitive data.
What is the importance of proactive security measures?
Proactive security measures are crucial in preventing security breaches. By implementing these measures, organizations can identify and address vulnerabilities before they are exploited by hackers.
What are some of the risks associated with security breaches?
Security breaches can lead to various risks, including data theft, loss of customer trust, financial losses, and damage to a company’s reputation. These risks can have long-lasting effects on the affected organization.
How can proactive security measures help prevent security breaches?
Proactive security measures involve continuous monitoring, identification of vulnerabilities, and timely implementation of security patches and updates. By taking these measures, organizations can strengthen their security infrastructure and reduce the risk of security breaches.







