In a shocking turn of events, the security systems of Orbiter Finance have been breached, exposing sensitive financial information of thousands of customers. This incident has not only raised concerns about the security measures in place but also highlighted the sophistication of modern hackers.
Orbiter Finance, a leading financial institution known for its robust security systems, was believed to be impervious to cyber-attacks. However, the recent breach has shattered this notion and left the company scrambling to mitigate the damage and restore trust among its customers.
The attackers, who exploited a vulnerability in Orbiter Finance’s network infrastructure, managed to gain unauthorized access to the company’s databases. This breach allowed them to extract sensitive information, such as financial transactions, account details, and personally identifiable information. The stolen data is believed to be valuable on the black market, putting the affected customers at risk of identity theft and financial fraud.
Investigations into the incident are ongoing, with cybersecurity experts trying to determine the exact modus operandi of the hackers. Initial analysis suggests that the breach was executed through a sophisticated combination of social engineering, malware, and targeted attacks.
Security Breach: A Prelude to the Attack

The Orbiter Finance systems security breach was not an isolated incident, but rather the result of a series of vulnerabilities and missteps that allowed hackers to gain access to sensitive data. This breach serves as a stark reminder of the importance of robust cybersecurity measures and constant vigilance.
Prior to the attack, several warning signs hinted at potential security vulnerabilities within the Orbiter Finance systems. These warning signs included outdated software versions, weak user authentication protocols, and inadequate monitoring and auditing procedures. These weaknesses provided an ideal entry point for hackers to exploit.
Furthermore, the lack of regular security audits and penetration testing allowed vulnerabilities to go unnoticed for an extended period of time. As a result, the hackers had ample opportunity to exploit these weaknesses, making the attack even more devastating.
Additionally, the lack of employee awareness and training in cybersecurity best practices played a significant role in this breach. Employees were not adequately trained to identify and report suspicious activities or phishing attempts. This lack of awareness allowed the attackers to successfully trick employees into revealing their credentials, further facilitating unauthorized access to the system.
In conclusion, the security breach at Orbiter Finance was not a sudden event but rather the culmination of various vulnerabilities and oversights within their systems. This breach serves as a reminder to organizations of the crucial need for robust security measures, regular audits, and continuous employee training to minimize the risk of cyberattacks.
Attack Vector: Exploiting Vulnerabilities
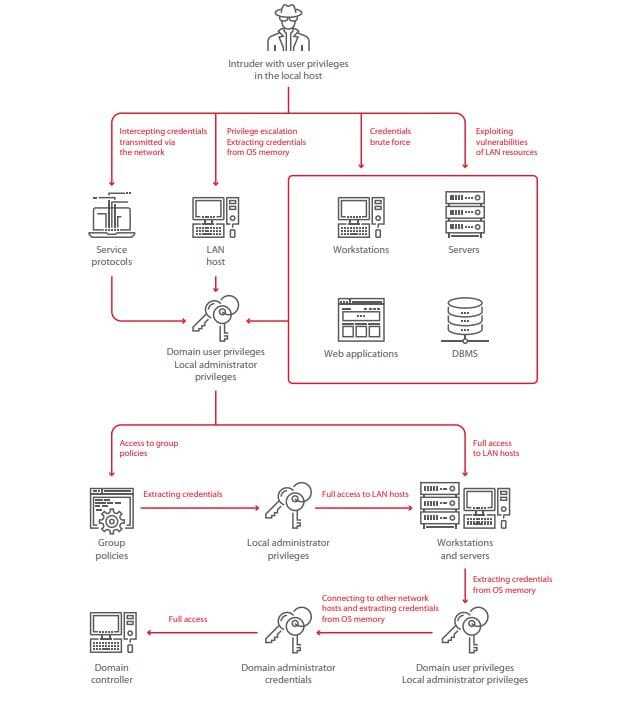
One of the primary ways in which the Orbiter Finance Systems were breached was through the exploitation of vulnerabilities in the system’s software and infrastructure. Attackers identified weak points in the system’s code, configuration, and network architecture that could be leveraged to gain unauthorized access and manipulate the system.
Vulnerable Software Components

The hackers identified several vulnerable software components within the Orbiter Finance Systems. These components had known vulnerabilities that could be exploited to gain control over the system. By targeting these specific components, the attackers were able to bypass the system’s security measures and gain access to sensitive data and resources.
Insecure Network Configuration

Another vulnerability that the attackers exploited was the insecure network configuration of the Orbiter Finance Systems. The network was not properly segmented, allowing the attackers to move laterally within the system once they gained initial access. This lack of network segmentation made it easier for the attackers to navigate through the system and access additional sensitive information.
| Vulnerability | Description | Impact |
|---|---|---|
| Unpatched Software | The system had outdated software versions with known vulnerabilities that had not been patched. | Allowed attackers to exploit known vulnerabilities and gain unauthorized access. |
| Weak Authentication | The system had weak authentication mechanisms, such as default or easily guessable credentials. | Allowed attackers to easily bypass authentication and gain privileged access. |
| Insufficient Logging | The system had inadequate logging and monitoring practices, making it difficult to detect and respond to intrusions in a timely manner. | Allowed attackers to remain undetected for an extended period and carry out their actions without being noticed. |
By exploiting these vulnerabilities, the attackers were able to gain unauthorized access to the Orbiter Finance Systems, compromise sensitive data, and carry out malicious activities without detection. This incident highlights the critical importance of regularly updating software, implementing strong authentication mechanisms, properly configuring network architecture, and maintaining robust logging and monitoring practices to mitigate the risk of unauthorized access and exploitation.
Breaching the Defense: Infiltrating Orbiter’s Systems

In order to execute the hack on Orbiter Finance Systems, the attackers employed a series of sophisticated techniques to infiltrate the company’s defenses. This section will delve into the various steps they took to breach the system and gain unauthorized access.
1. Reconnaissance: The attackers began by gathering intelligence about Orbiter’s infrastructure, network architecture, and potential vulnerabilities. They used this information to identify weak points that could be exploited.
2. Social Engineering: To gain initial access, the hackers utilized social engineering techniques to trick an employee into revealing their credentials or clicking on a malicious link. This allowed them to compromise a user account and gain a foothold in the system.
3. Exploiting Vulnerabilities: Once inside the system, the attackers exploited known vulnerabilities in Orbiter’s software, operating systems, or network infrastructure. They leveraged these weaknesses to escalate privileges, move laterally within the network, and gain access to sensitive data.
4. Privilege Escalation: With a compromised user account, the hackers actively searched for opportunities to escalate privileges and gain administrative access. This involved exploiting vulnerabilities in user privileges, misconfiguration of security settings, or weak password policies.
5. Persistence: The attackers established mechanisms to ensure continued access to Orbiter’s systems. They installed backdoors, created rogue user accounts, or planted malware that allowed them to maintain a presence even after initial access had been detected and revoked.
6. Covering Their Tracks: To avoid detection, the hackers carefully covered their tracks by deleting logs, modifying timestamps, and using encryption to obfuscate their activities. This made it difficult for security teams to identify and respond to the breach in a timely manner.
Understanding the techniques employed by the attackers is crucial for organizations to fortify their defenses and protect against future breaches. By implementing robust security measures, conducting regular audits, and staying abreast of emerging threats, companies can minimize the risk of unauthorized access to their systems.
Consequences and Lessons Learned: Aftermath of the Breach

When the breach of Orbiter Finance Systems occurred, it had far-reaching consequences for both the company and its clients. This section outlines the immediate and long-term effects of the breach and the lessons that can be learned.
Immediate Consequences

- Loss of sensitive data: The breach resulted in the unauthorized access to sensitive information such as customer personal data, financial records, and login credentials. This not only exposed the affected individuals to potential identity theft and fraudulent activities but also eroded trust in Orbiter Finance Systems.
- Financial losses: As a result of the breach, Orbiter Finance Systems faced significant financial losses. This included expenses related to investigating the breach, implementing security measures to prevent future attacks, and potential lawsuits and penalties.
- Reputation damage: The breach had a severe impact on the reputation of Orbiter Finance Systems. The company was seen as failing to adequately protect customer data, which led to a loss of credibility in the market. This, in turn, affected the company’s ability to attract new clients and retain existing ones.
Long-Term Consequences
- Regulatory scrutiny: Following the breach, Orbiter Finance Systems faced increased regulatory scrutiny. This included investigations from government authorities to assess the company’s compliance with data protection and privacy regulations. Non-compliance could lead to severe penalties and further damage to the company’s reputation.
- Customer attrition: As a result of the breach, some customers lost faith in Orbiter Finance Systems’ ability to protect their data. This led to customer attrition as clients switched to competitor services that they perceived as more secure. The loss of customers not only impacted revenue but also perpetuated the negative perception of the company.
- Increased security measures and costs: To regain trust and prevent future breaches, Orbiter Finance Systems had to invest heavily in improving its security infrastructure and implementing stricter protocols. This included hiring cybersecurity experts, conducting regular security audits, and implementing technologies such as encryption and multi-factor authentication. These increased security measures came with additional costs that had to be absorbed by the company.
Lessons Learned:
- Invest in proactive security measures: Orbiter Finance Systems learned the hard way that having reactive security measures is not enough. It is essential to invest in proactive measures to identify and prevent potential threats before they can cause harm.
- Educate employees and clients: Proper training and education on cybersecurity best practices for employees and clients are crucial in preventing breaches. Orbiter Finance Systems realized the importance of regularly educating its staff and customers about the risks of phishing attacks, weak passwords, and other common security vulnerabilities.
- Regular security audits and updates: Orbiter Finance Systems understood the value of conducting regular security audits and promptly applying software updates to address any vulnerabilities. This ensured that their systems were up to date and equipped to defend against evolving threats.
- Enhance incident response plan: The breach highlighted the need for an efficient and well-defined incident response plan. Orbiter Finance Systems developed a comprehensive plan that included predefined steps and responsibilities to mitigate the impact of future breaches and minimize response time.
In conclusion, the breach of Orbiter Finance Systems had severe consequences for the company and its clients. The aftermath of the breach led to financial losses, reputation damage, regulatory scrutiny, and increased security measures. However, the incident also served as a valuable lesson for Orbiter Finance Systems, prompting them to invest in proactive security measures, educate employees and clients, conduct regular security audits, and enhance their incident response plan to better protect against future breaches.
How did the hackers breach the Orbiter Finance Systems?
The hackers breached the Orbiter Finance Systems through a method called spear-phishing. They sent targeted emails to employees containing malicious attachments that, when opened, allowed the hackers to gain access to the system.
Were any customer data compromised in the breach?
Yes, customer data was compromised in the breach. The hackers were able to obtain personal information, such as names, addresses, and social security numbers, of some of the customers using the Orbiter Finance Systems.
What steps has the company taken to prevent future breaches?
The company has taken several steps to prevent future breaches. They have implemented multi-factor authentication for employees accessing sensitive systems, conducted cybersecurity training to educate employees about the risks of phishing attacks, and strengthened their firewall and network security measures.







