
Protect your financial data with Orbiter Finance’s cutting-edge security breach prevention strategies. Our team of experts utilizes advanced technologies and industry best practices to safeguard your sensitive information from cyber threats.
With the increasing number of cyber attacks, it is crucial for individuals and businesses to stay one step ahead of hackers. Orbiter Finance offers comprehensive solutions to counter cyber threats and minimize the risk of data breaches.
Our security breach prevention strategies include:
- Multi-factor authentication: Enhance the security of your accounts by implementing multi-factor authentication. This adds an extra layer of protection by requiring users to provide additional evidence of their identities.
- Encryption: Encrypting your data ensures that it remains unreadable to unauthorized individuals. Orbiter Finance utilizes state-of-the-art encryption techniques to protect your sensitive information.
- Regular security audits: Our team conducts regular security audits to identify vulnerabilities and address them proactively. By continuously monitoring and testing our systems, we ensure that your data is secure at all times.
- Employee training: We believe that a well-trained workforce is essential for maintaining robust security. Orbiter Finance provides comprehensive training programs to educate employees about the latest cyber threats and prevention techniques.
Don’t compromise on the security of your financial data. Choose Orbiter Finance’s security breach prevention strategies and stay protected from cyber threats.
Contact us today to learn more about our services and how we can help safeguard your sensitive information.
Proactive Measures for Preventing Security Breaches
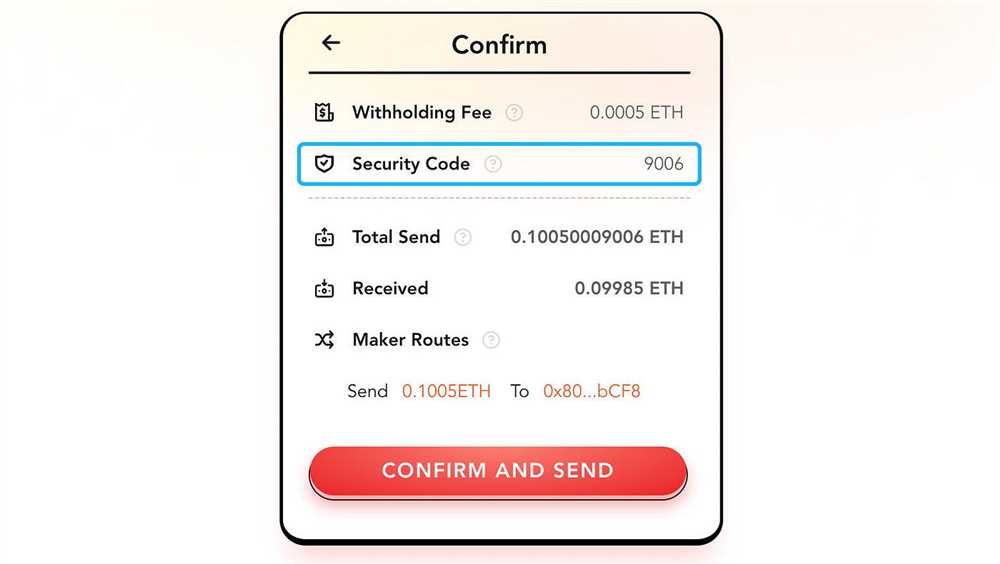
At Orbiter Finance, we understand the importance of ensuring the security and confidentiality of your sensitive data. That’s why we have implemented a range of proactive measures to prevent security breaches and safeguard your information.
1. Advanced Encryption: We utilize state-of-the-art encryption technologies to protect your data from unauthorized access. Our encryption algorithms provide a high level of security, ensuring that your information remains secure even if it falls into the wrong hands.
2. Multi-Factor Authentication: To add an extra layer of security, we employ multi-factor authentication. This requires users to provide multiple forms of identification, such as a password and a unique verification code, to access their accounts. By implementing this measure, we minimize the risk of unauthorized access to your sensitive data.
3. Regular Security Audits: We conduct regular security audits to identify any vulnerabilities or weak points in our systems. These audits help us proactively address any potential security risks, ensuring that our systems are robust and secure.
4. Employee Training: We believe that a strong security culture starts with well-trained employees. We provide comprehensive security training to all our staff members, educating them about the latest threats and best practices for preventing security breaches. By enhancing employee awareness and knowledge, we strengthen our overall security posture.
5. Secure Development Practices: When developing our software and systems, we follow secure coding practices. This ensures that our applications are resilient against common security vulnerabilities and reduces the risk of breaches due to coding errors or vulnerabilities. By prioritizing security during the development process, we minimize the potential attack surface.
6. Regular Updates and Patches: We keep our systems up to date with the latest security updates and patches. This includes applying updates to our operating systems, applications, and firewalls. By promptly addressing known vulnerabilities, we can protect against exploits and ensure that our systems remain secure.
At Orbiter Finance, we are committed to providing you with a secure and trustworthy platform to manage your financial information. Our proactive measures for preventing security breaches ensure that your data remains confidential and protected at all times.
Robust Authentication and Access Control
At Orbiter Finance, we understand the importance of protecting your sensitive financial information. That is why we have implemented robust authentication and access control measures to ensure the highest level of security for our clients.
Our authentication process involves multiple layers of security, designed to verify the identity of each individual user. We employ industry-standard protocols, such as two-factor authentication, to provide an extra layer of protection against unauthorized access.
In addition to strong authentication, we have implemented strict access control measures to safeguard your data. Our access control system is built to restrict unauthorized access and prevent potential security breaches. Only authorized personnel with the necessary credentials are granted access to our secure systems.
Furthermore, our access control system also includes role-based access control (RBAC) mechanisms. This means that different levels of access are granted based on an individual’s role within the organization. This ensures that employees only have access to the data and systems required for their specific job function, minimizing the risk of data exposure.
Key Features of Our Robust Authentication and Access Control System:

Multi-factor authentication: By combining something you know (password), something you have (authentication token), and something you are (biometric data), we ensure that only authorized individuals have access to your account.
Role-based access control: Our RBAC system allows for fine-grained control over access permissions, ensuring that each employee has access to only the necessary information and systems to perform their job duties.
Access logs and monitoring: We maintain detailed access logs and regularly monitor them to detect any suspicious activity or potential security breaches. This allows us to take immediate action and mitigate any security threats.
With Orbiter Finance’s robust authentication and access control measures in place, you can have peace of mind knowing that your financial information is secure and protected from unauthorized access.
Ongoing Monitoring and Incident Response

At Orbiter Finance, we understand the importance of ongoing monitoring and proactive incident response in maintaining the security of our clients’ financial data. We have implemented a comprehensive system that continuously monitors our network and infrastructure for any signs of security breaches or suspicious activity.
Our team of expert security analysts and engineers utilize state-of-the-art tools and technologies to constantly monitor and analyze the traffic and data flow within our systems. This allows us to quickly detect and respond to any potential security threats before they can cause significant damage.
In the event of a potential security breach, our incident response team immediately takes action to investigate and mitigate the situation. They follow a well-defined and rehearsed incident response plan, ensuring a swift and effective response to minimize any potential impact on our clients’ sensitive information.
Furthermore, we understand that effective incident response is not just about identifying and resolving security incidents, but also about learning from them to strengthen our security measures. Our incident response team conducts a detailed post-incident analysis, identifying any vulnerabilities or weaknesses that may have contributed to the incident. They then implement the necessary changes and enhancements to prevent similar incidents from occurring in the future.
With our ongoing monitoring and incident response capabilities, clients can trust Orbiter Finance to provide them with a secure and reliable platform for their financial needs. We are committed to staying at the forefront of technology and security best practices to ensure the highest level of protection for our clients’ data.
Employee Training and Awareness Programs

At Orbiter Finance, we understand that the greatest threat to the security of any organization comes from within. That is why we have implemented comprehensive employee training and awareness programs aimed at educating our staff about the potential risks and teaching them best practices for preventing security breaches.
Our training programs cover a wide range of topics, including but not limited to:
Identifying Potential Threats

Employees are trained to identify potential security threats, such as phishing emails, social engineering attempts, and suspicious behavior. By recognizing these warning signs, our employees are better equipped to take appropriate action and report any suspicious activities to our dedicated IT security team.
Safeguarding Data and Information
We provide training on how to handle sensitive data and information securely. This includes best practices for password management, encryption techniques, and the proper use of access controls. By ensuring our employees are well-versed in data protection protocols, we minimize the risk of accidental or intentional data breaches.
Regular Training Updates and Assessments
Our commitment to security extends beyond initial training. We conduct regular updates and assessments to ensure that our employees stay up to date with the latest security threats and protocols. This includes simulated phishing campaigns to test their awareness and readiness in real-world situations. Through ongoing training, we aim to foster a culture of security awareness throughout our organization.
Conclusion
At Orbiter Finance, we recognize that security breaches can have devastating consequences for businesses of any size. By investing in comprehensive employee training and awareness programs, we are committed to staying one step ahead of potential threats and safeguarding the confidentiality, integrity, and availability of our clients’ information.
What are the security breach prevention strategies used by Orbiter Finance?
Orbiter Finance implements several security breach prevention strategies to protect its systems and data. These include regular security audits and vulnerability assessments, strict access controls and authentication measures, encryption of sensitive data, implementation of firewalls and intrusion detection systems, and continuous monitoring of network traffic for any suspicious activity. Additionally, they conduct employee training and awareness programs to educate their staff about best practices for preventing security breaches.
How often does Orbiter Finance conduct security audits and vulnerability assessments?
Orbiter Finance performs security audits and vulnerability assessments on a regular basis, typically every six months or as required by industry standards and regulations. This helps identify any potential weaknesses or vulnerabilities in their systems or infrastructure and allows them to address them proactively to prevent security breaches.
What measures does Orbiter Finance have in place to ensure strict access controls and authentication?
Orbiter Finance implements a range of measures to ensure strict access controls and authentication. These include the use of strong passwords and two-factor authentication for accessing sensitive systems and data. They also employ role-based access controls, which means that employees only have access to the specific resources and information they need to perform their job functions. Orbiter Finance also regularly reviews and updates access privileges to prevent unauthorized access.
Does Orbiter Finance encrypt sensitive data?
Yes, Orbiter Finance encrypts sensitive data to ensure its confidentiality and prevent unauthorized access. They use industry-standard encryption algorithms and protocols to encrypt data both at rest and during transmission. This helps protect the data from being intercepted or accessed by malicious individuals or entities.
How does Orbiter Finance monitor network traffic for suspicious activity?
Orbiter Finance uses advanced network monitoring tools and technologies to continuously monitor network traffic for any signs of suspicious activity. This includes analyzing network logs, implementing intrusion detection systems, and utilizing artificial intelligence and machine learning algorithms to detect anomalies and potential security breaches. They also have a dedicated security operations center staffed with trained professionals who monitor and respond to any suspicious activity in real time.







