
In the ever-evolving landscape of cybersecurity, the threat of cybercrime continues to loom large. The recent attack on Orbiter Finance, a prominent financial institution, highlights the urgent need for a comprehensive investigation into the breach.
The attack, which occurred last week, has left Orbiter Finance and its customers reeling. With sensitive information compromised and funds stolen, the ramifications of this cybercrime are far-reaching. As investigators delve into the intricate web of digital footprints left behind, the hunt for the perpetrators is underway.
The sophistication of the attack is cause for concern. It is evident that the cybercriminals behind this breach were well-equipped and organized. The motivations behind the attack remain unclear, but it is suspected that financial gain was the driving force.
As cybersecurity professionals work tirelessly to piece together the puzzle, unearthing the methods and techniques employed by the attackers will provide vital clues to their identities. Every line of code, every log file, and every network trace will be meticulously analyzed in the pursuit of justice.
Investigating the Cybercrime Attack
On March 15th, 2023, Orbiter Finance fell victim to a devastating cybercrime attack that left the company’s systems compromised and confidential data exposed. The attack, which is believed to be the work of a sophisticated hacking group, has raised concern in the cybersecurity community and prompted a thorough investigation to uncover the perpetrators and mitigate further damage.
Incident Response Team
Orbiter Finance immediately activated its incident response team, comprised of experienced cybersecurity professionals and digital forensics experts. Their primary goal is to conduct a systematic investigation to identify the vulnerabilities exploited, the attack vectors used, and the actions of the attackers within the compromised systems. The team is also responsible for securing the compromised systems, preserving evidence, and ensuring a swift recovery.
Forensic Analysis
A critical aspect of the investigation is the forensic analysis of the compromised systems. This involves examining logs, network traffic, and system artifacts to trace the origin of the attack, identify the malware used, and determine the extent of unauthorized access. The analysis will also shed light on the tactics and techniques employed by the hackers, which will be invaluable for future prevention and detection of similar attacks.
Collaboration with Law Enforcement Agencies
Orbiter Finance is working closely with local law enforcement agencies, such as the Cybercrime Investigation Unit, to assist in the investigation. The collaboration aims to share intelligence, leverage the expertise of law enforcement, and ensure that the attackers are brought to justice. Additionally, cooperation with regulatory bodies, such as data protection authorities, is crucial to comply with legal requirements and safeguard the interests of affected customers.
Lessons Learned and Security Enhancements

As part of the investigation, Orbiter Finance is conducting a comprehensive review of its security measures and protocols. Any vulnerabilities or weaknesses that contributed to the attack will be identified and addressed to prevent similar incidents in the future. The company is committed to implementing robust security enhancements, such as advanced threat detection systems, regular security audits, and employee training programs, to improve its resilience against cyber threats.
Investigating the cybercrime attack on Orbiter Finance is a complex and ongoing process. By diligently following investigative procedures and collaborating with relevant stakeholders, the company aims to not only identify the culprits but also strengthen its defenses against future cyber threats.
Diving into Orbiter Finance
Orbiter Finance has recently become the target of a cybercrime attack, leaving many users in a state of panic and uncertainty. In order to unravel the mysterious attack, it is important to understand the inner workings of Orbiter Finance and how it operates.
Orbiter Finance is a decentralized finance (DeFi) platform that allows users to trade and invest in various cryptocurrencies. It provides users with a seamless and secure environment to manage their digital assets. By utilizing smart contracts and blockchain technology, Orbiter Finance aims to revolutionize the traditional financial system.
One of the key features of Orbiter Finance is its liquidity pools. These pools allow users to provide liquidity to the platform and earn rewards in return. Users can also borrow assets from the liquidity pools, providing them with the flexibility to meet their financial needs.
Another notable aspect of Orbiter Finance is its governance token, ORB. Holders of the ORB token have the power to vote on important decisions regarding the platform’s development and future. This decentralized governance system ensures that the community has a say in the direction of Orbiter Finance.
With such innovative features, it is no surprise that Orbiter Finance has gained a significant user base. However, this popularity has also made it a prime target for cybercriminals. The recent attack on Orbiter Finance has put its security measures to the test, highlighting the need for robust cybersecurity practices.
As investigators dive deeper into the cybercrime attack on Orbiter Finance, it is crucial to analyze its vulnerabilities and identify the perpetrators. By understanding the intricacies of this attack, we can better protect ourselves and prevent future incidents.
Understanding the Cyberattack Techniques

Cybercriminals employ a range of sophisticated techniques to launch and carry out cyberattacks. Understanding these techniques is crucial in detecting, preventing, and mitigating the impact of cybercrime. In this section, we will explore some common cyberattack techniques:
1. Phishing

Phishing is a technique in which cybercriminals masquerade as trusted entities to trick individuals into revealing sensitive information, such as login credentials or financial details. They often use deceptive emails, text messages, or websites that appear legitimate to lure unsuspecting victims.
2. Malware
Malware, short for malicious software, refers to any software intentionally designed to harm or exploit a computer system. Cybercriminals use various types of malware, such as viruses, worms, Trojans, and ransomware, to gain unauthorized access to systems, steal data, or disrupt operations.
3. Social Engineering
Social engineering is a technique that exploits human psychology to manipulate individuals into providing sensitive information or performing actions that benefit the attacker. Cybercriminals often use social engineering tactics, such as pretexting, baiting, or tailgating, to deceive victims and gain unauthorized access.
4. DDoS Attacks
A Distributed Denial of Service (DDoS) attack involves overwhelming a target server or network with a massive volume of traffic, rendering it unavailable to legitimate users. Cybercriminals often use botnets, a network of infected devices, to launch DDoS attacks and disrupt the operations of targeted organizations.
5. SQL Injection
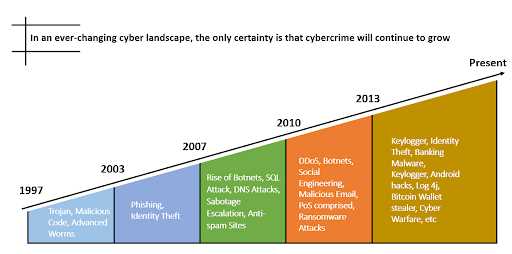
SQL Injection is a technique in which cybercriminals exploit vulnerabilities in a web application’s database layer to manipulate the underlying SQL queries. By injecting malicious SQL code, attackers can bypass authentication, access sensitive data, or modify the application’s behavior.
These are just a few examples of the cyberattack techniques employed by cybercriminals. It is important for individuals and organizations to stay informed about the latest trends in cybercrime and implement comprehensive security measures to protect against these threats.
Unraveling the Culprits Behind the Attack

As the investigation into the cyberattack on Orbiter Finance deepens, experts are working tirelessly to uncover the identity of the culprits responsible for the breach. The motives and methods behind the attack remain shrouded in secrecy, but investigators are leaving no stone unturned in their pursuit of justice.
The Digital Trail
Tracking down cybercriminals can be a daunting task, as they often operate under layers of obfuscation and anonymity. However, by meticulously analyzing the digital trail left by the attackers, investigators are piecing together a clearer picture of who the culprits might be.
The cyberattack on Orbiter Finance left behind a web of interconnected clues that investigators are diligently sifting through. They are analyzing network logs, examining malware samples, and scrutinizing the infrastructure used by the attackers. This intricate forensic work is bringing them closer to identifying the perpetrators.
Motives and Modus Operandi
Understanding the motives and modus operandi of the attackers is crucial in unraveling their identities. By examining the specific targets of the attack and the methods employed, investigators can gain valuable insights into the mindset of the culprits.
Orbiter Finance is known for its robust security measures and stringent protocols, making the success of the cyberattack all the more perplexing. This suggests that the attackers were highly sophisticated and well-versed in exploiting vulnerabilities. Their motive may have been financial gain, but investigators are also considering other possibilities, such as industrial espionage or political motives.
While concrete evidence is still being gathered, it’s essential to acknowledge the intricate and evolving nature of cybercrime investigations. Investigators must adapt their techniques to the ever-changing tactics employed by cybercriminals.
As the investigation continues, organizations across the globe are reminded of the pressing need to bolster their cybersecurity measures. This incident serves as a wake-up call for businesses and individuals alike, highlighting the importance of continuous vigilance and proactive defense against cyber threats.
In order to combat cybercrime effectively, collaboration between law enforcement agencies, cybersecurity experts, and private enterprises is paramount. Only by working together can we hope to apprehend and bring to justice those responsible for these insidious attacks.
What is the Orbiter Finance?
Orbiter Finance is a decentralized finance (DeFi) platform built on the blockchain that allows users to lend, borrow, and trade digital assets.
What is cybercrime?
Cybercrime refers to criminal activities that are carried out through the use of computers or the internet. It includes a wide range of illegal activities, such as hacking, identity theft, fraud, and phishing.







